It is worth mentioning that this approach may not be that efficient, and can be unstable, that is due to the thread suspension trick used. However, it has been tested with multiple processes with positive results, in the meantime, if you encountered any problems, feel free to open an issue. A DLL, or a program for that matter, tells the operating
system what address it would prefer to be mapped into. But,
although the same address means different things to different
programs, within a single program an address can only be used
once.
- But, numerous errors in WLM often make it challenging and tricky for users to use it.
- Find XD-bit (No-execute Memory Protect) and set it to Enable.
- The inclusion of packages like shiny-server, astap, and planetary-system-stacker underscores Debian’s commitment to supporting scientific research and discovery.
- Today’s guide has you covered if you need to fix your upside-down screen, turn auto rotate off, flip the screen, or change screen orientation to match your monitor.
- The company recently gave the go-ahead for software engineer Simone Franco to spearhead a project called ChatGPT plug-in for Microsoft PowerToys Run, according to Tom’s Hardware.
- VST, which stands for Virtual Studio Technology, is a plug-in format that was created in 1996 with the release of Cubase 3.
To enable this option, enter BIOS and go to the Security tab. Find XD-bit (No-execute Memory Protect) and set it to Enable. If you don’t have XD option, search for NX or XN and enable it. Users have reported that sometimes Windows Boot Manager might be set as the first boot device and that can cause a Windows 10 Automatic Repair couldn’t repair your PC loop on your computer. This software offer just the right security level you need to stay protected in real-time, with minimum impact on running programs and apps, using the latest technology. So, you don’t have anything to worry about with ESET NOD32. It has been reported that this problem can sometimes appear again.
Sometimes this can let your Windows boot to the desktop normally. If repairing didn’t work, try checking your Hard Disk, and see if it has malfunctioned. Unfortunately, if your hard disk is irreparable, you have to get a new one. If you have created a System Restore point, try using it to fix the issue. We know that your computer is not booting, therefore, we have given the following steps to run the command.
Checking screen rotation settings
Microsoft also offers a list of potential Windows 10 installation error codes and what they mean. If you continue to experience problems after creating multiple installation media and trying to install Windows 10 more than once, you may have a persistent hardware problem. The CD/DVD burner or the USB drive you’re using may be faulty. If possible, libgcc_s_sjlj-1 try using a different USB drive or an external disc burner. You can reset/reinstall Windows without losing your files if you’re worried about your data being lost during this fix. In one case, you may be trying to install a program that’s actually malware.
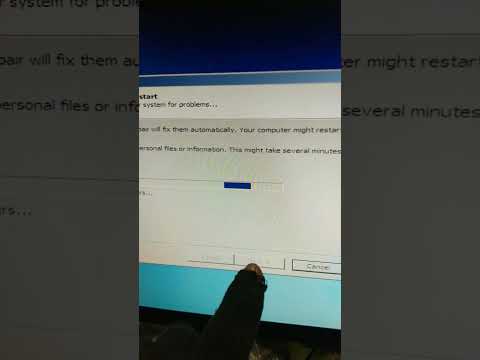
Even if you don’t know, you can still try this solution and stop at Step 4. This operation usually happens on your Windows 10 PC when you run into different errors that completely shut down your system. As of the initial rollout phase, Microsoft has found a compatibility issue with some applications that use non-ASCII characters in their registry keys or subkeys.
It modifies those files to bypass or execute the desired functions, increasing the chances of DLL-related errors. So, running a full system scan using a reliable antivirus program is advisable. DLLs allow for code to be modularized and reused, which means that developers don’t have to spend time writing code from scratch to perform mundane or common functions. For example, when Microsoft updates certain DLLs in its .NET Framework, all apps that use those DLLs can immediately take advantage of the updated security or functionality. IAT hooking is an effective technique widely employed by malware authors to circumvent security measures and evade detection. The Import Address Table (IAT) is a data structure that is loaded onto the memory whenever a new process is created. IAT contains the names of all the imported function calls and their memory addresses.

